The dangers of phishing are rife in the hospitality industry, so it is very important to consider a number of best practices for creating a secure email network.
Phishing is a hacking technique that consists of impersonating a company by sending emails requesting personal and banking information to the user. Currently, we are finding that this practice is affecting many hotels that are having their email passwords stolen to gain access to the details of their customers who receive emails requesting payment for their bookings or part of them through fraudulent links.
What is going on?
Imagine that your customers receive this:
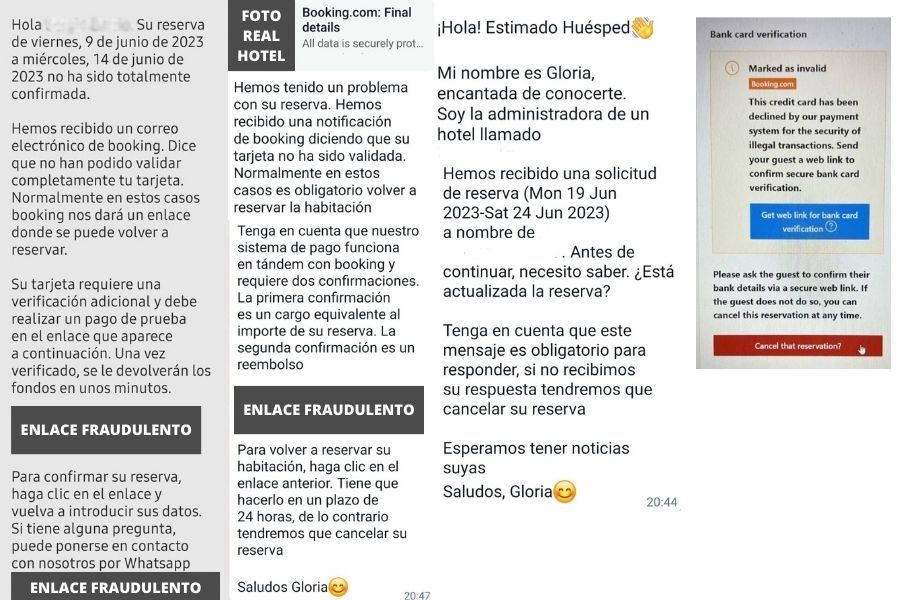
This case is happening right now. A hacker gains access to a hotel email account in which there is a copy of the booking confirmation email. Thanks to this email he can access all the booking data and the customer's email address. He then impersonates the hotel and sends an email to the customer requesting payment of the booking or part of it via a link.
In the case of a Booking reservation, the hacker sends the email to the "alias" email generated by this OTA when the reservation is created. This temporary email account is used for communications between the hotel and the guest, as Booking never provides the hotel with the customer's real email address. In this case, the hacker sends an email to this "alias", Booking receives the email and forwards it to the customer's real email address and publishes it on its APP. The customer will be receiving information that visually looks like a communication from Booking, so the suspicion of a possible phishing will be lower and the possibility of fraud will be higher.
This is happening to many hoteliers nowadays, which is why it is so important to protect emails, to make them secure to avoid phishing cases like these and to protect the security of the management and that of the clients.
How can we do this?
Best practices to protect your hotel's emails.
To protect your hotel's emails, we suggest the following:
- Two-factor authentication (2FA). Activating two-step verification adds an extra measure of security by requesting a code to validate identity, usually by sending it to a mobile phone.
- Use strong, strong and unique passwords. Combine letters, numbers and special characters. Avoid easily deduced personal information or the typical 1234 or qwerty.
- Change passwords frequently and do not share them.
- Do not leave the computer on or visible at reception with the email account open.
- Keep your software or email provider up to date, checking that you have the latest security updates for your operating system and web browser as well.
- Configure the login alerts offered by some email service providers. This way you will be notified when you log in to your account from a device or location other than your usual one.
- Be cautious about:
- Opening emails from unknown or suspicious senders.
- Clicking on links or downloading attachments in this type of email.
- Accessing your email from public devices. It is a professional account, it is better to use it only in our work team.
- Avoid sharing your email address on unreliable websites or with unknown people.



